Risk Based Security reported that 8 billion records were compromised by 5,207 data breaches in 2017. The average breach costs companies $3.62 million (€2.69 million), according to global research conducted by Ponemon Institute for their 2017 Cost of Data Breach Study: Global Overview. Contributing to that hefty tab are legal defense fees, regulatory noncompliance penalties, data breach notification costs, revenue losses from increased customer turnover, and the expense of repairing a damaged reputation.
Stipulating how sensitive information must be handled and preventing the potentially devastating consequences of a data breach are central to the numerous privacy regulations in effect throughout the world. These measures compel organizations to protect personal identifiable information in all its forms, including electronic data, or be subject to substantial fines. Global standards that exist are just the minimum requirements expected from IT asset disposition vendors. Other security measures vary depending on the client and their unique needs.
Where data lurks
The actions of hackers and negligent employees or contractors were responsible for more than 918 data breach incidents globally in the first half of 2017. With so much at stake, most data security efforts are justifiably focused on protecting electronic equipment currently in use. These devices are subject to clearly defined security procedures that protect the equipment and the data they contain from intrusion, loss and unauthorized access.
Electronics marked for disposal
On occasion, computers and other electronic devices marked for disposal fall outside those established security protocols even though they may still contain easily accessible data that can leave an organization vulnerable to a data breach incident.
This data exists not just in computer and server hard drives that have been declared obsolete or redundant, but across a wide array of devices including copiers, printers, scanners and fax machines. Two office workhorses—copiers and printers—often have hard drives that store readily obtainable data and can be the unexpected source of a data breach.
For corporate data security experts, protecting the data on all devices is the foundation of their data security policies and procedures. Most people are aware of the significant data security risks posed by failing to eliminate information from computer and server hard drives and understand the need to destroy the data on these devices.
Solid state drives
Devices equipped with solid-state drives look similar to traditional magnetic hard drives but are often smaller, more durable and store data on flash memory chips which have no moving parts. Solid-state drives require special processing to ensure all data has been removed. For instance, an absence of magnetic components makes solid-state drives impervious to degaussing. Also, currently available hard drive wiping techniques may give the appearance of complete data erasure during verification, but recoverable data may remain due to the unique recording storage and organizational characteristics of this technology. It is important to validate that any data destruction methods being implemented are truly removing all data from the solid state drive on the flash translation layer and all sectors.
Mobile devices
A growing number of employees who are allowed to use their own mobile devices, such as smartphones or tablets, to connect to corporate networks, email accounts or file-sharing applications can also put confidential data at risk. Whether company or employee-owned, mobile devices have computing power and data storage capacity that rival some desktop and laptop machines. Their size and popularity however make them more vulnerable to loss and theft, substantially increasing the data security risk posed by mobile technology.
Unlike computers and servers whose contents are subject to strict security protocols retired, broken, or employee-owned mobile devices sometimes fall outside the scope of these policies, setting up the possibility of a data breach. Also keep in mind that many smartphones and tablets are equipped with solid-state technology, making them subject to the same data erasure challenges as other devices using this technology to record, store and access data.
Assessing the risk
It comes as no surprise that data can be stored and accessed in more places than ever, but not all IT assets are created equal. As an IT asset manager, it is important to understand which IT assets bear more risk than others and which types of threats exist with each.
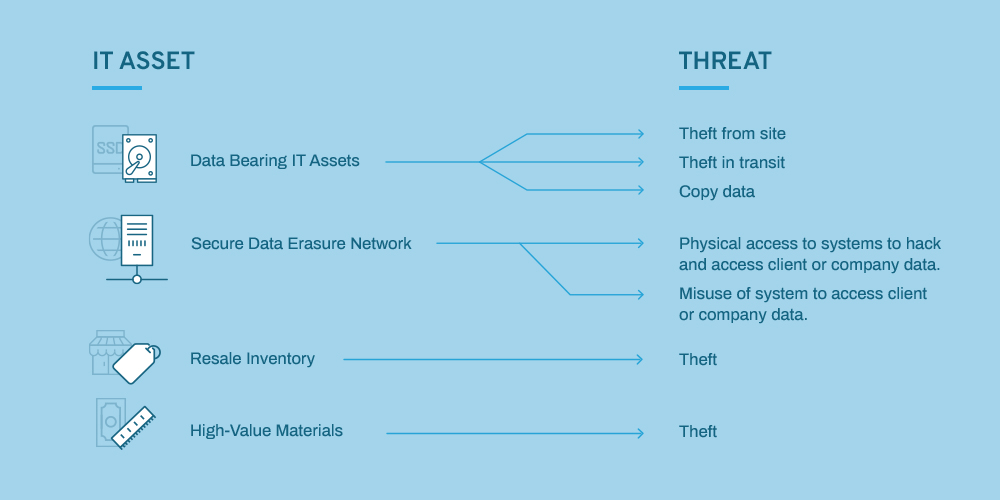
When managing retired IT and electronic equipment, physical theft is going to be of primary concern. Physical theft as opposed to systems hacks are prevented in different ways. When questioning your vendor’s security systems, you can start by reviewing their certifications. If you want to take it a step further there are things you can look for in a vendor beyond security certifications. Read our recent blog post for more information about what you need to look for, beyond certifications, to mitigate ITAD security threats.
Learn more about ITAD security standards to look for.
